Maximizing Cybersecurity Investments for Small and Medium-Sized Businesses
Every day small and medium-sized businesses (SMBs) face increasing cyber threats. Despite limited resources, SMBs need to allocate their...
.png)
In the current digital environment, small and medium-sized businesses (SMBs) are not exempt from cyber threats. Recent data highlights the growing risk faced by these businesses. Cybersecurity for SMBs is now as crucial as it is for large enterprises. The statistics from the Verizon Data Breach Investigations Report (DBIR) and Keeper Security's research reveal that SMBs are increasingly becoming targets for cyberattacks.
To combat this alarming trend and safeguard their assets, SMBs must adopt proactive measures, and one powerful tool in their arsenal is the cybersecurity risk assessment. This process involves identifying, analyzing, and evaluating the daily risks faced by the organization. By understanding potential vulnerabilities and their potential impacts, SMBs can ensure the implementation of effective cybersecurity controls and tools to respond to cyber threats. The cybersecurity risk assessment covers various critical areas that require attention and action. These include:
1. Technology: The core infrastructure of most SMBs is heavily reliant on technology. To secure it effectively, implementing regular device and software updates is crucial. Additionally, having up-to-date antivirus and antimalware software, along with network segmentation and encryption protocols, can further bolster the defenses against potential attacks. A layered approach to cybersecurity, which includes perimeter security, endpoint security, backup and disaster recovery, and real-time monitoring, adds an extra layer of protection.
2. Policies: Policy measures form the foundation of a cyber-secure corporate culture. Implementing and enforcing access control policies, multi-vendor endpoint management policies, and policies for Bring Your Device (BYOD) scenarios can minimize security risks originating from within the organization. Having a robust business continuity and disaster recovery plan, along with considering cybersecurity insurance, provides added protection against unforeseen events.
3. People: Employees are often considered the weakest link in cybersecurity. Providing visible incident reporting channels, comprehensive end-user training, and integrating cybersecurity training and awareness into the organizational culture can significantly reduce the human element's potential to compromise security.
By addressing these areas comprehensively and systematically, SMBs can create a robust framework to protect against potential cyber-attacks. Cybersecurity risk assessments should be an ongoing and recurrent process, allowing SMBs to continually strengthen their defenses and foster a cyber-safe culture within the organization.
In conclusion, cybersecurity risk assessments are not optional for small to medium-sized businesses; they are a necessity. The ever-evolving threat landscape demands proactive measures to protect sensitive data and critical infrastructure. By understanding the potential risks and vulnerabilities, implementing appropriate security controls, and fostering a culture of cybersecurity awareness, SMBs can better defend themselves against cyber threats and safeguard their future success.
Every day small and medium-sized businesses (SMBs) face increasing cyber threats. Despite limited resources, SMBs need to allocate their...
.png)
Cyber risk management has become a crucial part of overall risk management strategies in the modern world, as organizations rely primarily on...
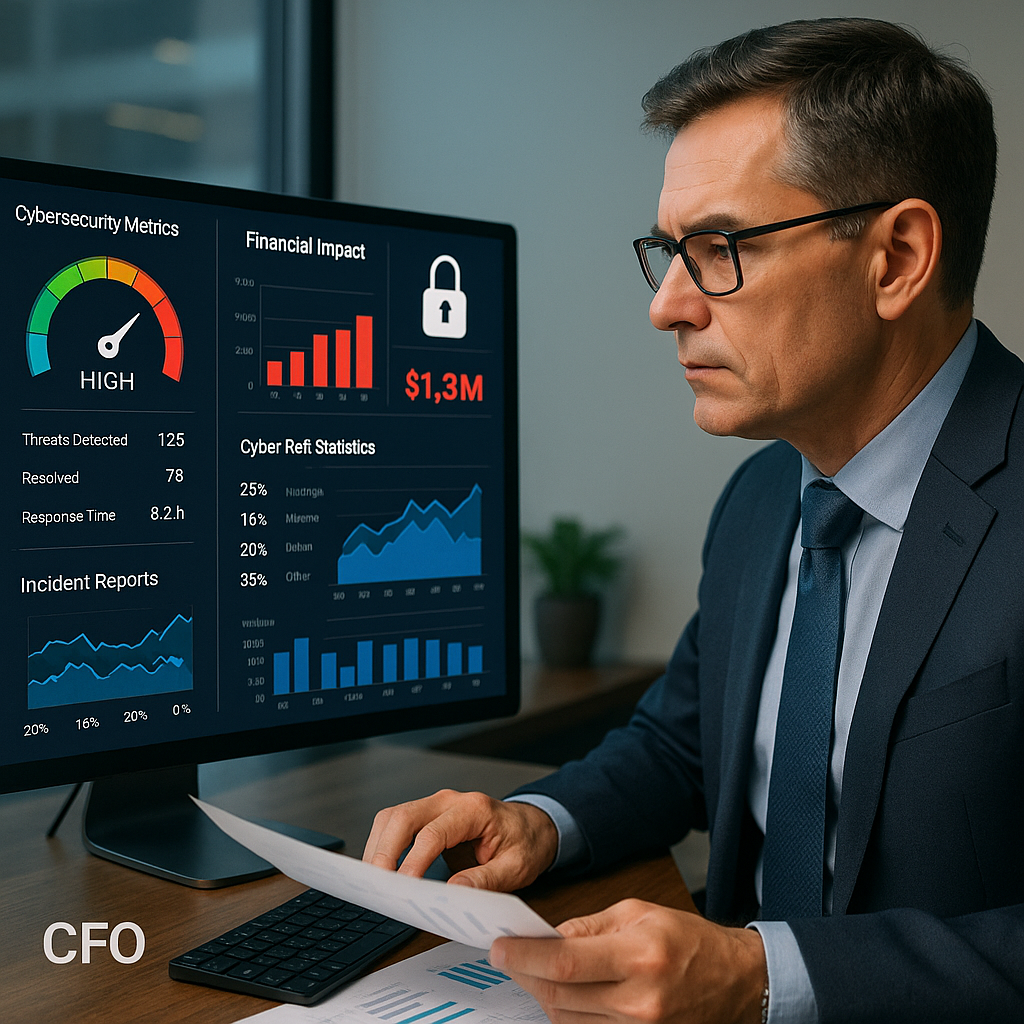
As cyber threats increasingly impact financial performance and business continuity, CFOs are emerging as critical partners in building resilient...