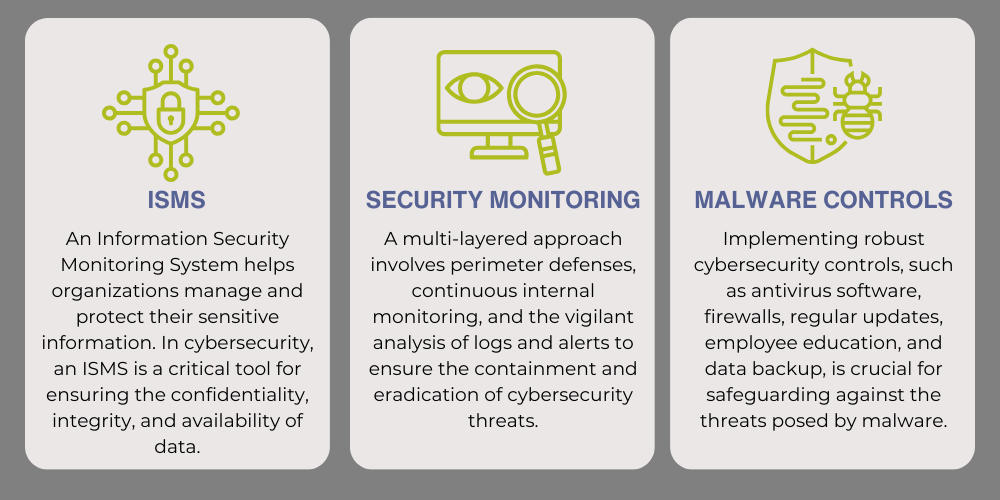
security operations
SECURITY OPERATIONS
Cybersecurity operations are crucial for safeguarding digital landscapes. Positioned at the frontline of defense, these teams monitor, detect, and respond to security incidents, maintaining constant vigilance over network activities and implementing protective measures. Using sophisticated technologies like intrusion detection systems and firewalls, coupled with skilled human interpretation of data, these operations play a paramount role in ensuring the resilience of interconnected digital infrastructures.

Real-time analysis and triage of immediate threats, when something goes wrong.
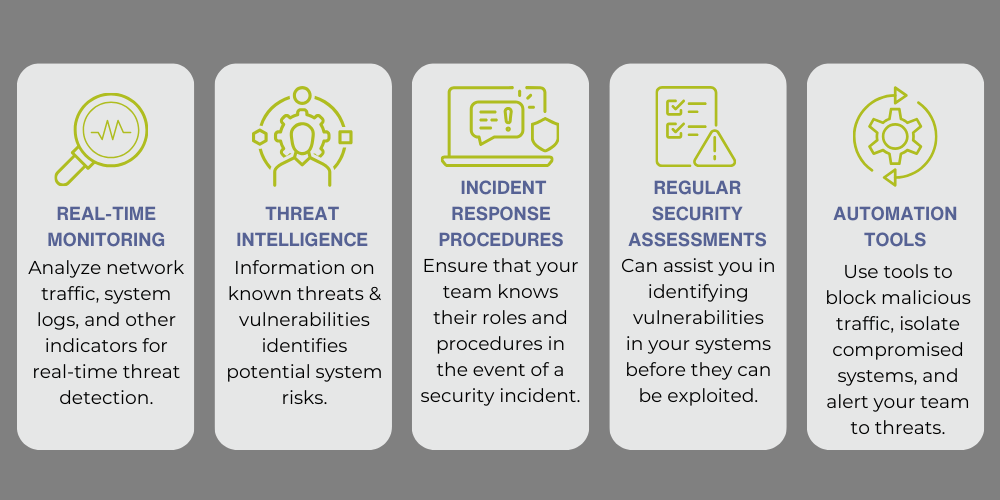
Incident Management
Effective incident management requires a well-defined plan that outlines the roles and responsibilities of the incident response team, the steps to be taken in response to a security incident, and the communication protocols to be followed during the incident.
.png?width=700&height=350&name=Incident%20Management%20(2).png)
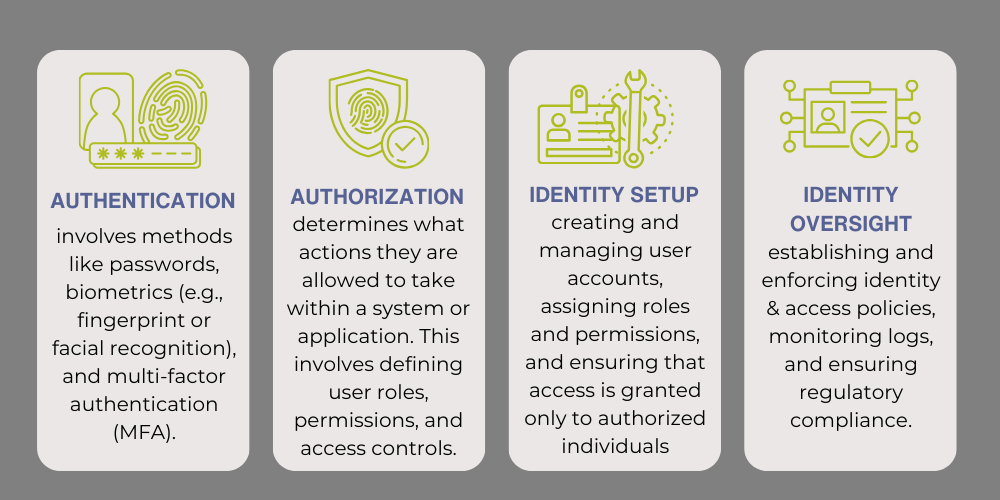
Identity Management
Identity management is a critical aspect of cybersecurity operations. It involves the processes and technologies to manage and secure digital identities, including user accounts, passwords, and other authentication credentials.
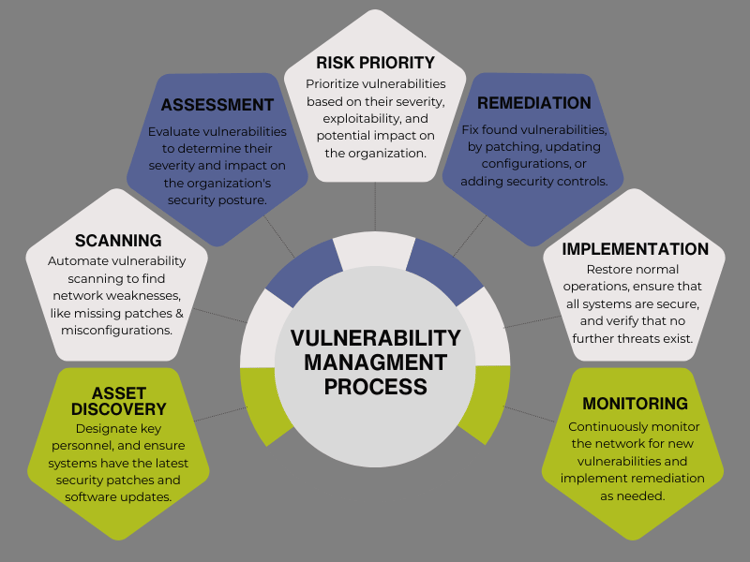
Vulnerability Management
Vulnerability management is a crucial component of cybersecurity that involves identifying, assessing, prioritizing, and mitigating security vulnerabilities in an organization's IT infrastructure. The process is designed to help organizations reduce the risk of cyber-attacks and data breaches by addressing known vulnerabilities promptly and effectively.
Additional factors to take into account in cybersecurity operations...