regulatory compliance
Cybersecurity compliance is essential for SMBs, requiring adherence to standards like GDPR, HIPAA, and PCI DSS. It’s more than a legal obligation—it’s a key strategy for protecting sensitive data and maintaining customer trust. By implementing strong security measures, staying updated on regulations, and conducting regular assessments, SMBs can reduce risk, avoid costly penalties, and strengthen their overall cybersecurity posture.
-1.jpeg?width=300&height=168&name=images%20(1)-1.jpeg)
SOC, ISO AND CMMC
SOC (System and Organization Controls), ISO (International Organization for Standardization), and CMMC (Cybersecurity Maturity Model Certification) are frameworks aiding organizations in establishing and maintaining information security and cybersecurity standards.
These frameworks collectively offer organizations a roadmap to effectively implement and uphold cybersecurity measures. Adherence to these standards is instrumental in safeguarding sensitive data, preserving customer trust, and mitigating potential financial and legal consequences arising from cybersecurity incidents.

Data privacy is a growing priority in U.S. cybersecurity.
With more than 20 states enacting their own privacy laws—many focusing on consent, data access, and breach notifications—businesses must adopt strong security and transparency practices to stay compliant and build trust. While laws vary, most require clear data handling policies, user rights, and safeguards for personal information. A flexible, proactive approach to privacy is essential to keeping pace with this evolving regulatory landscape.
GAP ASSESSMENT
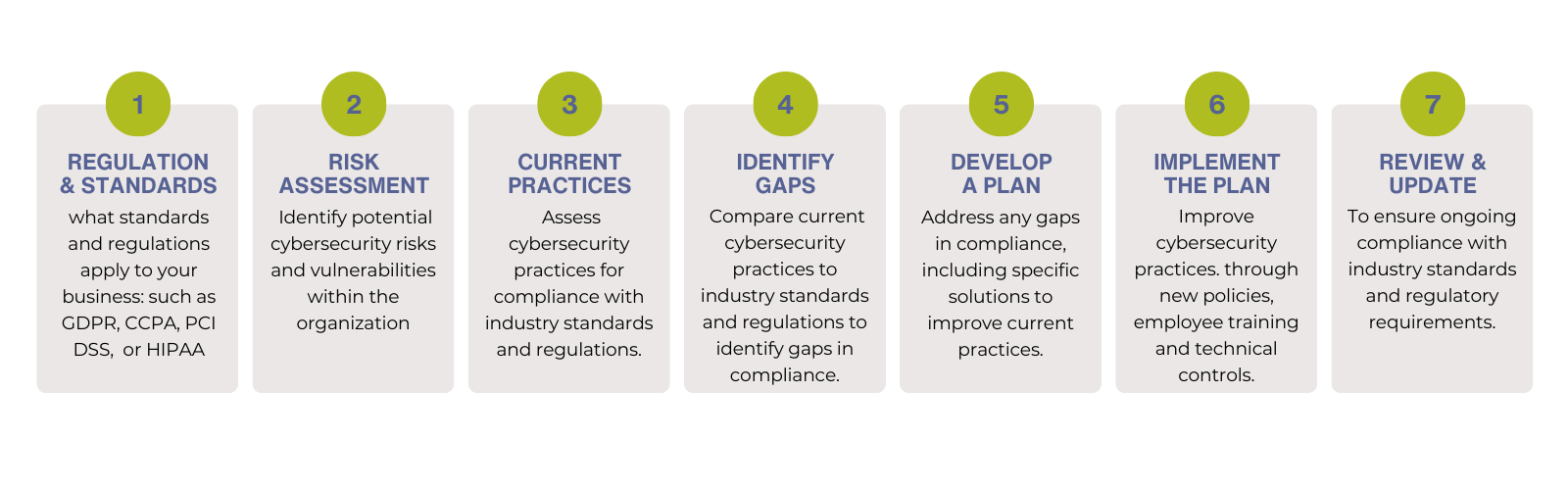
A cybersecurity GAP assessment evaluates current practices to identify weaknesses and compliance shortfalls. It helps uncover risks and guides improvement efforts to meet industry standards.
To get started, follow these steps:
ACCREDITATION, AUDIT AND ATTESTATION
Accreditation, audit, and attestation are vital elements of cybersecurity regulation that collectively contribute to securing information systems and data. These processes work in tandem to guarantee the security of information systems, ensuring organizational compliance with relevant cybersecurity regulations and standards.

CONTRACTUAL NEEDS
Clear cybersecurity terms in contracts ensure all parties understand their responsibilities for protecting sensitive data. Aligning on standards and expectations helps maintain compliance and reduce cyber risk. Key considerations include:

