strategy, leadership & governance
strategy, leadership & governance
In cybersecurity, the synergy of strategy, leadership, and governance forms the foundation for robust defense against digital threats. A well-crafted strategy outlines goals and resource allocation, leadership fosters a cybersecurity-centric culture, and governance provides the framework for decision-making and risk management. Together, these pillars create a resilient cybersecurity posture, allowing organizations to navigate the digital landscape with confidence.

Security Governance
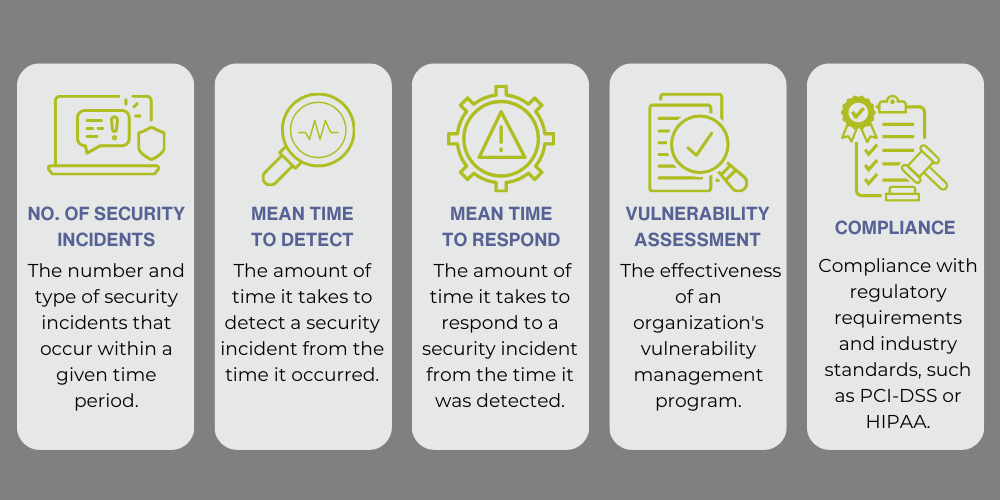
Security governance encompasses the policies, procedures, and frameworks organizations employ to identify and mitigate risks related to their IT systems and data. It entails the creation, implementation, and management of strategies to safeguard information assets and critical infrastructure from unauthorized access, theft, or damage.
Effective cybersecurity governance requires collaboration among all stakeholders, including executive management, IT staff, legal and compliance teams, and employees. Key components involve risk assessment, policy development, compliance monitoring, incident response planning, and continuous improvement.
Common frameworks for cybersecurity governance include the National Institute of Standards and Technology (NIST) Cybersecurity Framework, ISO/IEC 27001, and the Payment Card Industry Data Security Standard (PCI DSS).
.png?width=900&height=400&name=Security%20Governance%20(3).png)
Policy And Procedures
Cybersecurity policies and procedures encompass a set of guidelines and practices adopted by an organization to safeguard its computer systems, networks, and data against unauthorized access, theft, or damage. These measures are critical for upholding the confidentiality, integrity, and availability of the organization's information assets. Tailored to address the specific risks and requirements of the organization, these policies and procedures should undergo regular review and updates to maintain their effectiveness. The key elements integral to cybersecurity policy and procedures include:
Metrics & Reporting
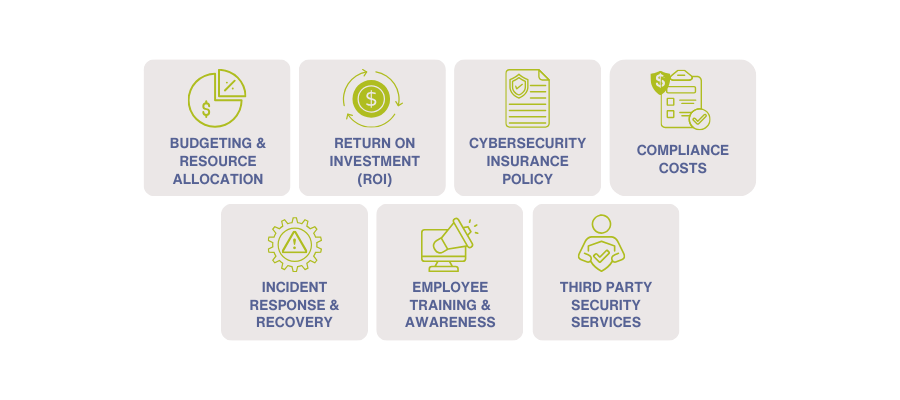
In a cybersecurity program, metrics play a crucial role in measuring and quantifying different aspects of performance, including the number and severity of security incidents, the success rate of security controls, and the security program's overall effectiveness. Subsequently, reporting involves the clear and concise communication of this information to stakeholders such as executives, board members, and regulatory bodies.
Finance
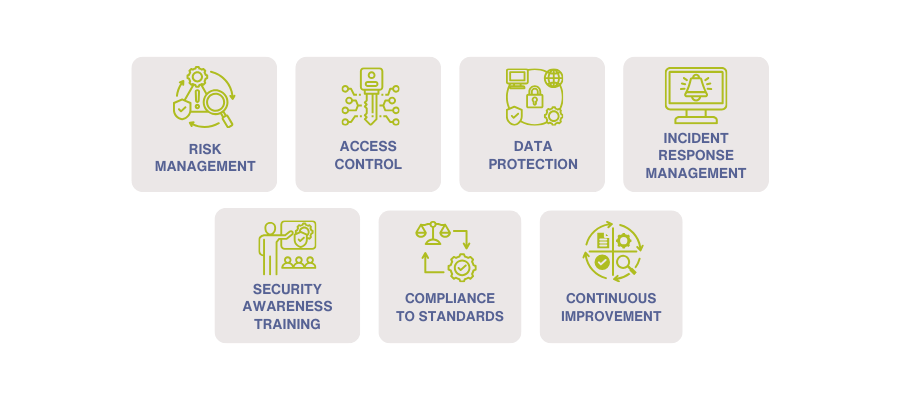
The financial landscape of a Small to Medium-sized Business (SMB) is intricately intertwined with cybersecurity concerns, necessitating a strategic approach to safeguard both fiscal resources and digital assets. Investments in cybersecurity technologies, personnel training, and incident response capabilities become paramount to mitigate financial risks associated with potential cyber threats. Regulatory compliance further shapes the financial strategy, ensuring adherence to industry standards and avoiding potential financial penalties. As cyber threats evolve, the adaptability of cybersecurity measures becomes essential for maintaining the financial resilience and sustainability of the SMB in the digital age.