risk management
RISK MANAGEMENT
Continuous improvement in cybersecurity risk management is crucial for safeguarding against constantly evolving cyber threats. Organizations must continually assess and update their security measures to mitigate the risks of data breaches and cyber-attacks.
Regularly identifying weaknesses and vulnerabilities can help prevent malicious actors from exploiting them. Implementing new strategies and technologies can help organizations stay ahead of emerging threats and maintain a robust cybersecurity posture. Organizations can ensure the safety and security of their valuable assets and information by prioritizing continuous improvement in cybersecurity risk management.

Risk Management Framework
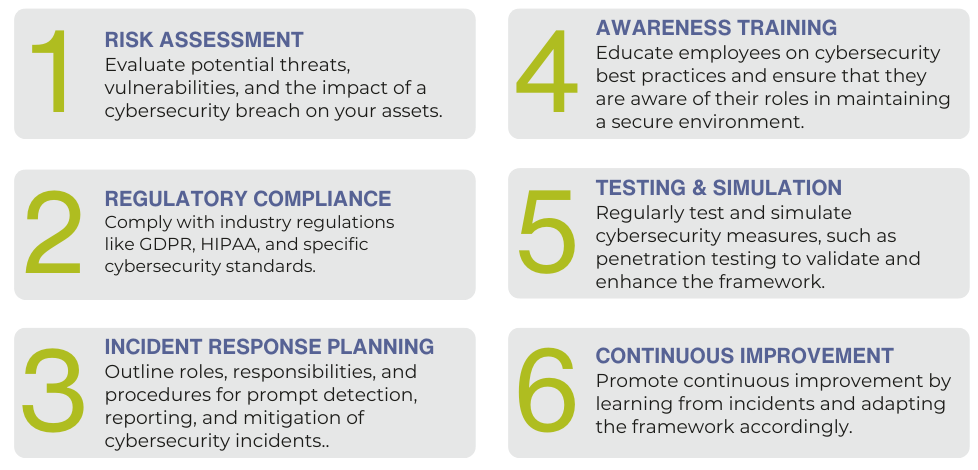
The Risk Management Framework (RMF) is a structured approach to managing risks in cybersecurity. It provides a comprehensive and systematic process for identifying, assessing, prioritizing, and managing risks to information and information systems. The RMF consists of six steps:
Continuous Improvement
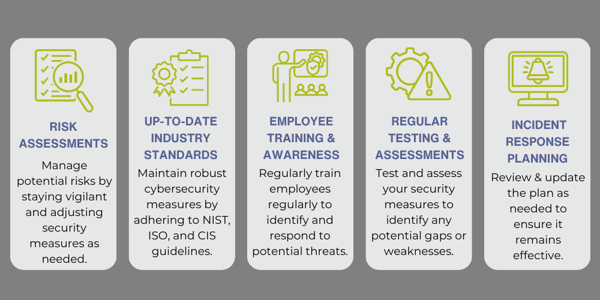
Continuous improvement is an essential aspect of cybersecurity risk management. With the constantly evolving nature of cybersecurity threats, it is crucial to continually reassess and improve your security measures to stay ahead of potential risks.
Here are some steps you can take to ensure continuous improvement in your cybersecurity risk management:
Threat Assessment
Threat assessments involve identifying, analyzing, and evaluating potential threats to an organization's information systems, networks, and data. The aim is to assess the associated risk levels and formulate strategies for mitigating these risks. Through this process, organizations can prioritize and address significant cyber risks, thereby reducing their overall cybersecurity risk.

Vulnerability Assessment
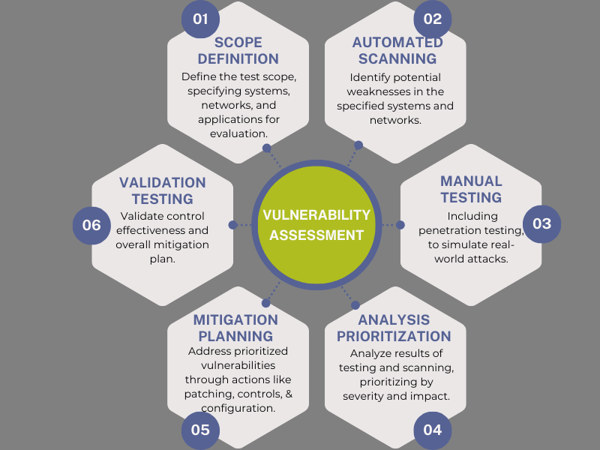
A cybersecurity vulnerability assessment is a systematic examination of an organization's digital infrastructure to identify potential weaknesses or vulnerabilities that could be exploited by malicious actors. This assessment typically involves analyzing systems, networks, and applications to discover and prioritize security risks. The goal is to enhance overall security by mitigating or eliminating identified vulnerabilities. Vulnerability assessments often include penetration testing, security scans, and analysis of security controls to ensure a proactive and effective approach to cybersecurity.
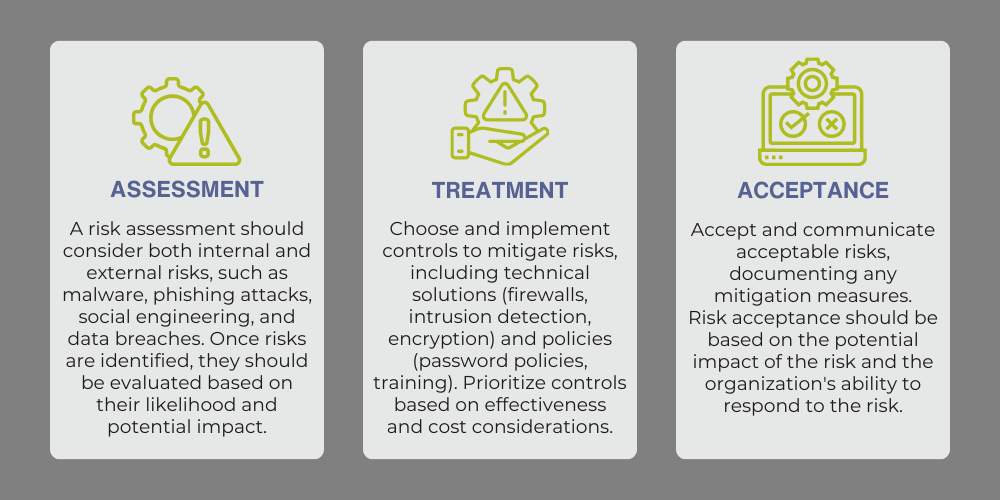
Risk Assessment, Treatment & Acceptance
Effective cybersecurity management requires a continuous process of risk assessment, treatment, and acceptance. By regularly assessing and addressing cybersecurity risks, organizations can better protect themselves from cyber threats and minimize the potential impact of any incidents that do occur.