How to Prevent Supply Chain Attacks on Your Small Business
In today's digital age, small businesses are increasingly vulnerable to sophisticated cyber threats, including supply chain attacks that exploit...
2 min read
.jpeg) Michael Markulec
:
Sep 22, 2023 4:25:00 PM
Michael Markulec
:
Sep 22, 2023 4:25:00 PM

Cyberattacks pose a serious and ongoing threat to the manufacturing sector in today's rapidly changing technological environment. This sector's vulnerability arises from its intricate supply chain, the wealth of intellectual property it holds, and the sensitive data it processes. The consequences of a successful cyberattack on a manufacturing firm can be severe, encompassing substantial financial losses and reputational damage.
Although prevalent across industries, phishing attacks have shown a notable uptick within manufacturing. These insidious attacks often take the form of malicious email attachments or deceptive website links, leading to the deployment of malware. The ultimate goal: gathering valuable data for ransom or sale on the dark web. The manufacturing industry's susceptibility to phishing attacks is exacerbated by several factors. Legacy equipment, fragmented security infrastructure, and a diverse workforce with varying levels of IT training all contribute to this vulnerability. Manufacturers engaged in government contracts can be particularly attractive targets for threat actors. To mitigate this threat, organizations must fortify their cybersecurity measures with multiple layers of defense and integrate awareness training into their corporate culture.
Malicious software, called ransomware, encrypts sensitive information, making files, databases, and applications inaccessible. Attackers subsequently demand a ransom in exchange for the decryption key. The ramifications of a ransomware attack on manufacturing can be dire, resulting in production disruptions, delivery delays, and substantial revenue losses. Manufacturers must implement cybersecurity best practices, maintain round-the-clock network monitoring, and prioritize cybersecurity awareness training for all employees. Additionally, regular security assessments should be conducted to proactively counter ransomware threats.
Manufacturers heavily rely on their intellectual property (IP) to gain a competitive edge and fuel innovation. IP theft can inflict significant harm, including loss of competitive advantage, financial setbacks, damage to reputation, and potential legal consequences. Threat actors, adept at infiltrating manufacturing systems, can quietly abscond with data, leaving behind minimal traces. Protecting IP necessitates proactive measures such as restricting sensitive information access and monitoring for unauthorized access or suspicious activities.
Manufacturers depend on an intricate network of suppliers, partners, and vendors to source raw materials, components, and finished products. Cybercriminals often target these partners to gain access to a manufacturer's systems, potentially leading to data theft or operational disruptions. Caution is advised when sharing financial, intellectual, or operational data with partners. A single employee at a supply chain partner falling prey to a phishing email can grant hackers access to private networks and sensitive information. Prevention measures encompass regular security assessments, access controls, anti-virus and anti-malware software deployment, and appropriate physical security measures.
The Internet of Things (IoT) is gaining prominence in manufacturing, with smart machines and sensors connecting to the Internet to enable automation and data analytics. However, this connectivity exposes manufacturers to new security risks. To mitigate these threats, manufacturers must implement robust IoT security measures, including the use of secure IoT devices, network segmentation, and continuous monitoring of IoT device activity.
In conclusion, the manufacturing industry remains a prime target for cyberattacks, given its complex supply chain and the valuable assets it possesses. Therefore, investing in cybersecurity should not be seen as an option but as an integral part of a company's culture and business continuity plan. Recent surveys indicate that manufacturers are increasingly recognizing the evolving cybersecurity landscape's significance, a trend that will be crucial in the years ahead.

In today's digital age, small businesses are increasingly vulnerable to sophisticated cyber threats, including supply chain attacks that exploit...
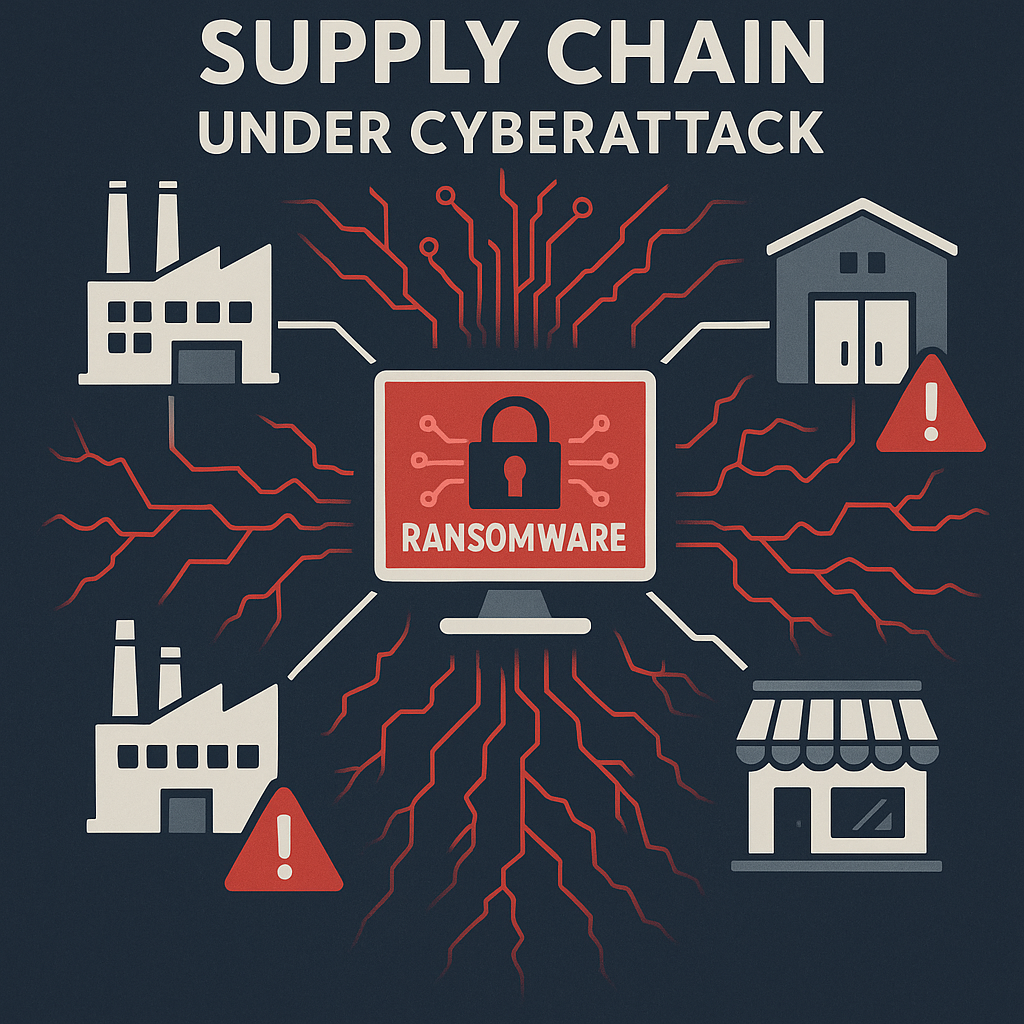
Ransomware threats are rapidly evolving, now employing sophisticated tactics to infiltrate supply chains and disrupt entire business ecosystems,...

When we think about cybersecurity, the digital defense systems, tools, hardware, and knowledge that fight cybercrime, we don’t often think about the...