The Importance of Threat Intelligence Reports for Businesses
In an era of constantly evolving cyber threats, threat intelligence reports have become essential for businesses seeking to protect their digital...
4 min read
.jpeg) Michael Markulec
:
Jan 14, 2026 10:30:00 AM
Michael Markulec
:
Jan 14, 2026 10:30:00 AM
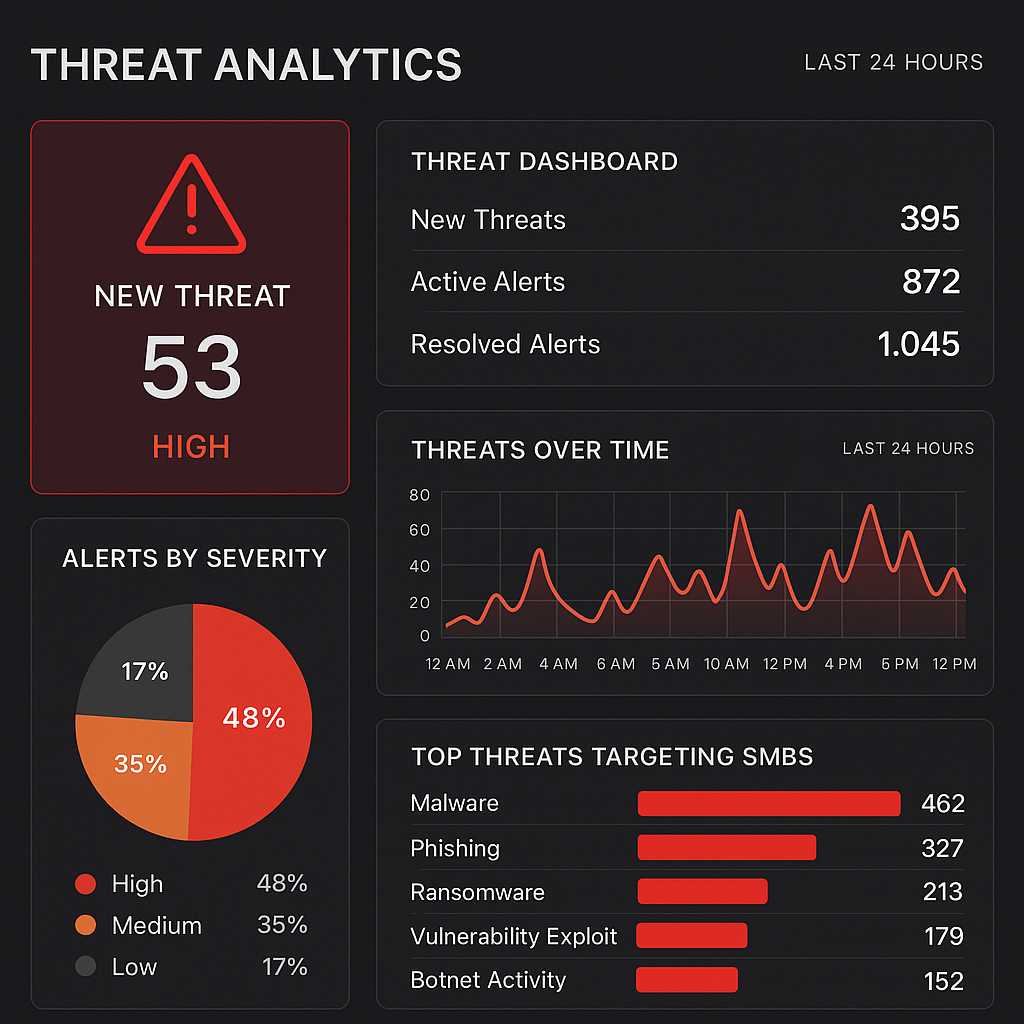
Discover how the latest threat intelligence trends are reshaping cybersecurity strategies for small and midsize businesses, and what actionable steps your organization can take to stay ahead of emerging risks.
Small and midsize businesses (SMBs) are increasingly in the crosshairs of sophisticated cyber adversaries. Recent intelligence indicates that cybercriminals are leveraging artificial intelligence (AI) and automation to execute attacks at scale, with no distinction by company size. Tactics such as ransomware-as-a-service, business email compromise, and supply chain exploits are being customized to target SMBs, often exploiting their resource constraints and limited cybersecurity staffing.
This evolution in attacker capabilities is closing the gap between opportunistic and highly targeted campaigns. Threat actors can now rapidly profile organizations, scrape publicly available data, and tailor social engineering lures to specific roles, geographies, and technologies in use. For SMBs accelerating digital transformation, adopting cloud services, and integrating with new platforms, this means that every new system, integration point, and vendor relationship becomes a potential attack surface.
The use of AI by threat actors enables more convincing phishing campaigns, intelligent malware that evades detection, and rapid exploitation of newly discovered vulnerabilities. Machine-generated content can mimic internal communication styles, impersonate executives or trusted vendors, and dynamically adjust based on user behavior, significantly increasing the likelihood of a successful compromise. Automated scanning and exploit frameworks also allow attackers to weaponize zero-day and n-day vulnerabilities against thousands of targets in minutes.
This shift signals a growing need for SMBs to adopt proactive, intelligence-driven security strategies to counteract these evolving risks. Rather than relying solely on basic perimeter defenses or ad hoc security measures, organizations must incorporate continuous threat monitoring, timely intelligence feeds, and regular risk assessments into their security programs. Aligning security controls with current threat trends—such as hardening identity and access management, improving email security, and validating the security posture of third-party providers—enables SMBs to focus limited resources on the risks most likely to impact their business.
Threat intelligence reports consistently highlight several recurring vulnerabilities within SMB environments. Weaknesses in remote access solutions, outdated software, insufficient patch management, and misconfigured cloud services remain primary attack vectors. Additionally, the growing reliance on third-party vendors and managed service providers (MSPs) introduces new risks, as attackers often exploit these relationships to gain access to multiple organizations through a single point of compromise.
Credential theft, phishing, and brute-force attacks on remote desktop protocols are increasingly common, particularly as more SMBs embrace hybrid work models. The lack of multi-factor authentication (MFA) and inconsistent network segmentation further exacerbate exposure to these threats.
To effectively mitigate these emerging threats, SMBs should prioritize a layered security approach informed by current threat intelligence. Implementing MFA across all critical systems, enforcing strong password policies, and regularly updating software are foundational steps. These controls should be complemented with robust endpoint protection, secure configuration baselines, and continuous monitoring to quickly identify and contain anomalous activity before it escalates into a business-impacting event. For organizations operating in cloud and hybrid environments, hardening identity and access management, enabling conditional access policies, and regularly reviewing privileged accounts are essential components of this layered defense.
Conducting ongoing security awareness training, including phishing simulations, can significantly reduce the risk of successful social engineering attacks. Training should be tailored to different roles and functions, emphasizing real-world attack scenarios observed in current threat intelligence reports. Reinforcing this with clear incident-reporting procedures, simulated business email compromise scenarios, and executive-focused tabletop exercises helps build a security-aware culture in which employees act as an extension of your detection capabilities rather than a recurring vulnerability.
Leveraging virtual Chief Information Security Officer (vCISO) services can provide SMBs with the strategic guidance, risk assessments, and policy development typically reserved for larger enterprises, but at a scale and cost appropriate for smaller organizations. A vCISO can help translate threat intelligence into a prioritized security roadmap, align controls with frameworks such as NIST CSF and CMMC, and ensure that security investments are tightly aligned with business objectives and regulatory requirements. Regular vulnerability assessments, business continuity testing, and incident response planning ensure ongoing resilience and rapid recovery in the event of an attack. When combined with managed security services for 24/7 monitoring, detection, and response, these measures enable SMBs to move from reactive firefighting to proactive, intelligence-driven risk management that supports long-term growth.
Forward-thinking SMBs recognize that robust cybersecurity is not just a defensive measure—it is a key enabler of business growth and competitive differentiation. By integrating security into core business processes and decision-making, organizations can confidently pursue digital transformation, expand into new markets, and build trust with customers and partners. When security teams and business stakeholders are aligned on shared objectives—such as customer experience, revenue growth, and operational resilience—security becomes a strategic asset that accelerates execution.
Embedding security into technology selection, vendor due diligence, and product development helps SMBs move faster with less risk. For example, incorporating security requirements into procurement and contract negotiations reduces downstream remediation costs, while building secure-by-design principles into new services shortens sales cycles by meeting customer and regulatory expectations from day one. In regulated industries or when handling sensitive customer data, demonstrable security controls can directly influence win rates, partnership opportunities, and the ability to participate in higher-value ecosystems.
Adopting a security-driven mindset supports regulatory compliance, enhances operational efficiency, and reduces the potential for costly disruptions. By standardizing controls, policies, and response procedures, organizations can streamline audits, avoid duplication, and create repeatable processes that scale with the business. Mature security operations—such as centralized logging, continuous monitoring, and documented playbooks—also reduce mean time to detect and respond, limiting the financial and reputational impact of incidents.
Partnering with trusted cybersecurity advisors, such as vCISO providers and managed security services, allows SMBs to align their security investments with broader business objectives, ensuring both protection and sustainable growth. These partners can interpret threat intelligence in the context of your specific environment, quantify business risk in terms executives understand, and build a pragmatic roadmap that balances cost, compliance, and resilience. For many SMBs, this means gaining access to enterprise-grade expertise, 24/7 monitoring, and structured governance without the overhead of a whole in-house security team—transforming cybersecurity from a necessary expense into a driver of confidence, innovation, and long-term competitive advantage.

In an era of constantly evolving cyber threats, threat intelligence reports have become essential for businesses seeking to protect their digital...

Discover how Microsoft Sentinel can be a game-changer for your small business's cybersecurity strategy.
.png)
In an era of ever-evolving digital threats, the recent cyberattacks on significant companies like Stop & Shop and AT&T highlight the crucial need for...